MetaDefender Sandbox and AI: Redefining Threat Detection
Discover how AI-powered services enhance our sandbox, enabling advanced detection capabilities. We explore intricate details, showcase real-world cases, and demonstrate how AI-driven features dynamically adapt to evolving threats with precision.
In cybersecurity, even the smallest vulnerability can lead to major breaches. Organizations must move quickly to keep pace with evolving technology and social trends, requiring advanced, adaptive, and intelligent solutions.
One such solution is MetaDefender Sandbox™, now reinforced by the power of (AI) Artificial Intelligence.
With its ability to analyze, predict, and mitigate cyber risks, MetaDefender Sandbox™ is leading a paradigm shift in how we think about digital security, protecting critical assets at an unprecedented level.
Why Sandbox Systems Need AI?
Traditional sandboxing has been crucial for malware detection, but it’s no longer enough, as attackers are refining their techniques, becoming more elusive and increasingly dangerous.
Early sandboxes relied on dynamic analysis, executing files to observe their behavior. In time, evasive malware outsmarted this method. To keep up, sandbox systems must evolve, and AI plays a critical part in this evolution.
Modern sandboxes—those that integrate AI with both static and dynamic analysis, emulation, and threat intelligence—can detect highly obfuscated threats like ransomware and zero-day exploits.
AI enables proactive, predictive defense, learning from past threats to spot new ones before they cause harm.
We’ve embraced this evolution, combining AI with advanced analysis techniques to improve accuracy and efficiency.
Our solution goes beyond dynamic analysis, applying AI-driven insights to detect and mitigate complex threats more effectively.
Read this article for a deeper look into the evolution of sandboxing and how AI reshapes threat analysis.
AI-powered Solutions’ Landscape in MetaDefender Sandbox™
Similarity Search for Threat Hunting
Why does it matter?
As cybercriminals fine-tune their methods, traditional signature-based systems became less effective—particularly against repackaged malware with minor modifications.
The Similarity Search tool enables threat hunters to actively search for files similar to known malicious ones.
Security teams gain a crucial advantage in identifying and neutralizing sophisticated attacks by actively searching for similarities in malicious files, which helps detect emerging threats early.
Flagging newly crafted or altered malware strains strengthens overall security and speeds up response times.
How It Works
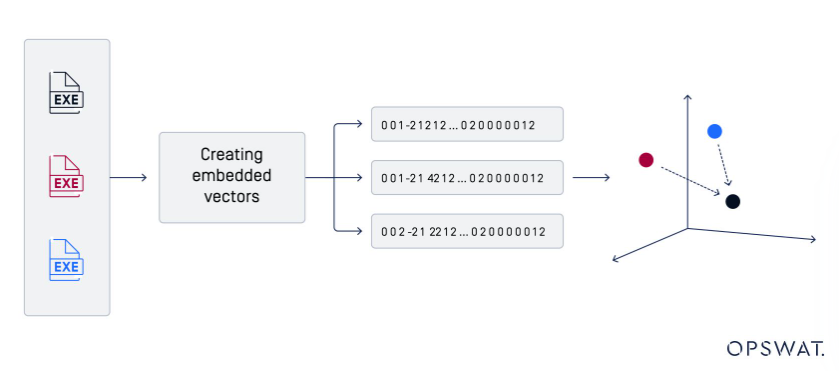
The Sandbox extracts various features from files and, using advanced distance calculations, compares them against a vast database of known files.
Even slight variations in structure or metadata are detected, revealing potential threats and providing threat hunters with the tools to detect evolving threats and improve their abilities.
Advanced Detection: Unlike signature-based systems, which rely on exact matches, Similarity Search can detect even small differences between files.
Real-World Applications: This enables the identification of previously unknown threats and makes zero-day detection possible by recognizing patterns and anomalies that haven’t been formally documented yet.
Outcome
The market lacked a threat-hunting tool capable of suggesting similar files based on their intrinsic characteristics.
This gap in available security tools meant that threats with slight variations could easily slip through the cracks.
With the introduction of Similarity Search, threat hunters can now actively search for potential emerging threats by comparing files with known malicious ones.
Being able to detect subtle, evolving threats before they cause harm improves both detection and response times. This makes Similarity Search an indispensable tool for modern cybersecurity defenses.
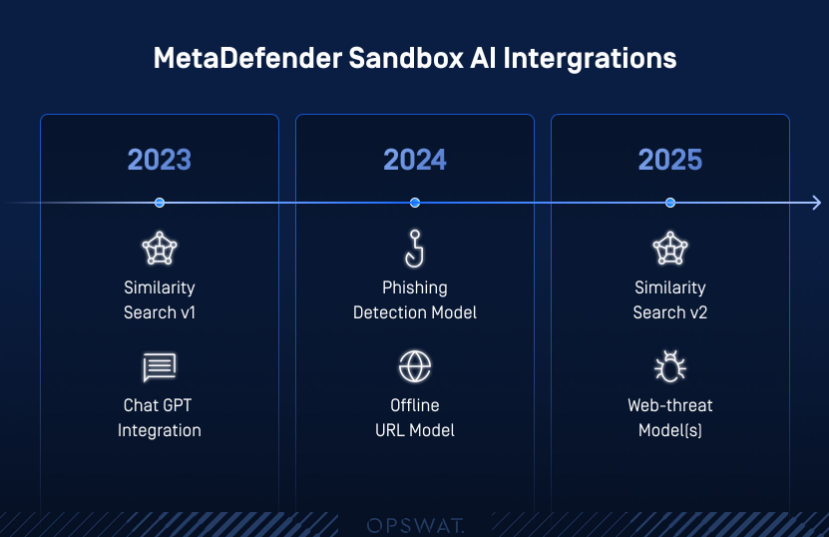
We’ve updated Similarity Search multiple times since its first release.
Initially, we supported only PE files with some limitations.
Since then, we’ve added more features, supporting better comparisons between .NET files, and improved our logic for better results.
By the first quarter of 2025, we will support not just PE files, but all kinds of files—find more info here.
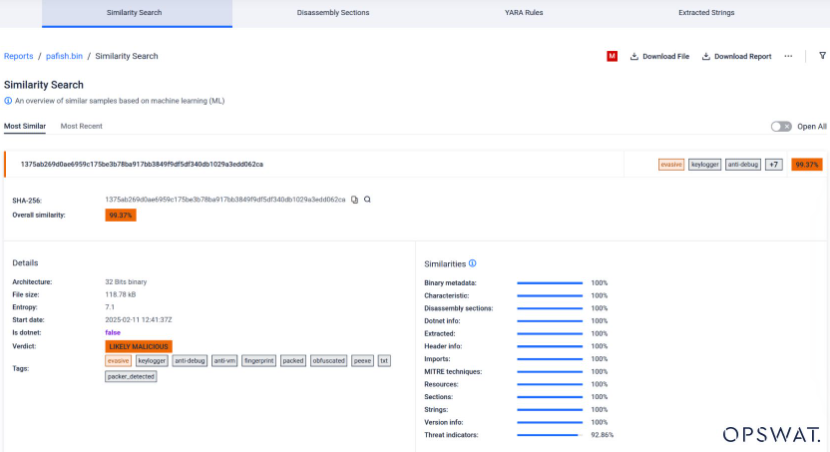
How to use the Similarity Search tool in MetaDefender Sandbox™
- Open the Sandbox Page and scan a file.
- Click on “Similarity Search” to access the tab.
- Adjust filters, such as search thresholds and verdicts, to refine your search.
- View search results.
- Expand file hashes for more details: click on a hash to view detailed information about the similarities.
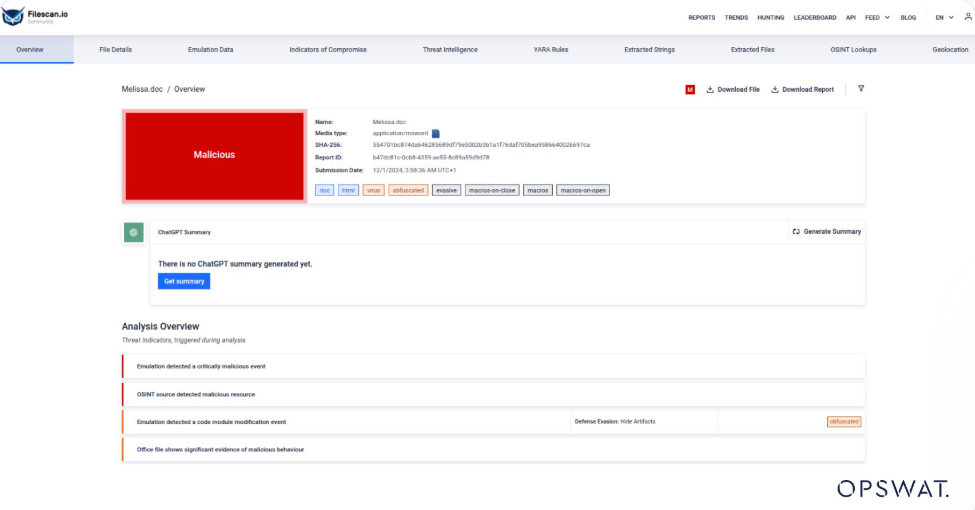
Executive Summaries via ChatGPT Integration
Why does it matter?
In a (SOC) Security Operations Center, two key metrics directly impact a company’s ability to respond to threats: (MTTD) Mean Time to Detect and (MTTR) Mean Time to Remediate.
Faster detection and remediation reduce the potential damage from cyber incidents, helping with breaches and data loss prevention.
However, SOC teams often face alert fatigue and resource constraints, which can slow down response times.
This is where our ChatGPT integration makes a difference. ChatGPT uses (NLP) Natural Language Processing to simplify complex and technical malware reports into easy-to-understand summaries.
Clearer summaries help SOC teams prioritize threats more efficiently, save time, and ultimately improve both MTTD and MTTR.
Additionally, streamlined report analysis helps teams to respond faster, reduce burnout, and better protect their assets.
ChatGPT was an innovation we viewed as an opportunity to simplify threat analysis and improve SOC efficiency for faster, more accurate responses to cybersecurity incidents.
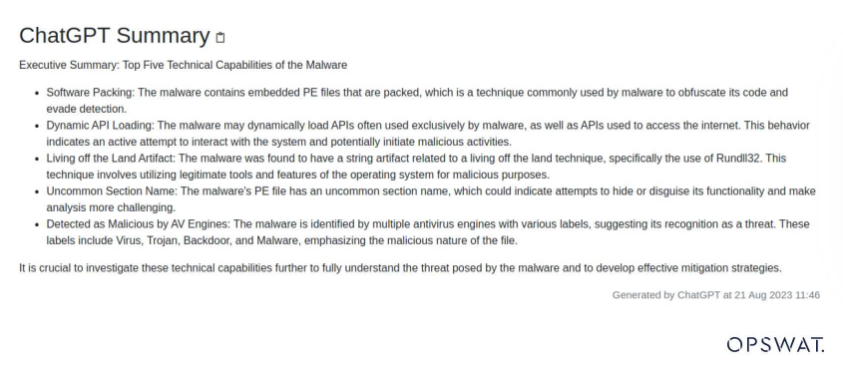
Example
A 20-page technical analysis of a ransomware attack is condensed into a one-paragraph executive summary, highlighting the attack vector, affected systems, and recommended actions.
Outcome
Decision-makers can better and quicker assess threat levels, without needing to dive deep into technical details. This speed also translates into faster and more informed responses.
How to use Executive Summaries in MetaDefender Sandbox™
- Open the Overview Page
- Click on the “Get Summary” button to generate a ChatGPT summary.
- ChatGPT will gather relevant information about the file, providing an executive summary of its potential malware capabilities.
Fore more detailed settings, check out this resource.
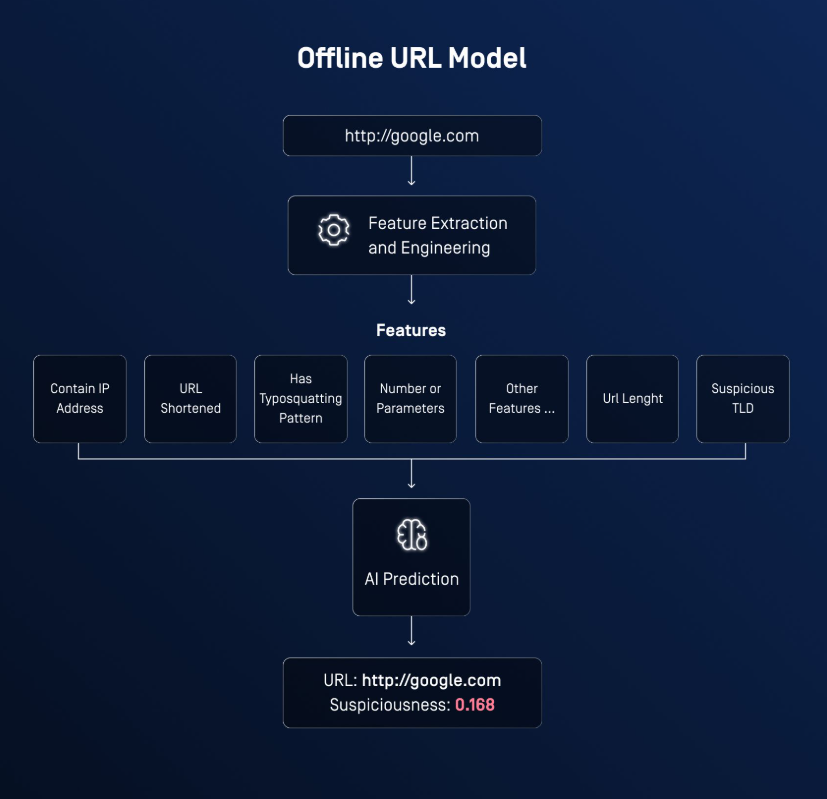
Offline URL Model for Suspicious URL Detection
Why does it matter?
We asked ourselves: can we create an offline model that analyzes a URL and determines whether it’s suspicious?
Our URL model is trained on an extensive dataset of 1.6 million URLs, extracting a wide range of features from URL strings.
It predicts the suspiciousness of a URL on a scale from 0 to 1, giving security teams the ability to avoid URL-borne risks before they get a chance to escalate.
The model is incredibly fast and has achieved over 93% accuracy at the 0.5 threshold.
Depending on the situation, you can adjust the threshold and detection will be further refined to reduce false negatives.
How It Works
The model extracts many features from the URL string, then uses a value between 0 and 1 to predict URL suspiciousness.
Impact
The model works on air-gapped systems and is incredibly fast.
It provides an essential first layer of phishing or malicious URL detection. You can get more information on the subject here.
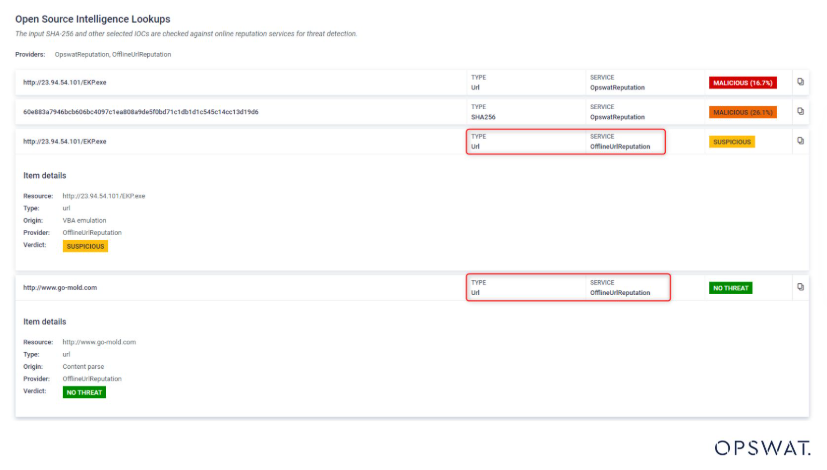
How to use the Offline URL Model in MetaDefender Sandbox™
The Offline URL model is called with each submission to assess whether a URL is suspicious or not, by default.
You can find this feature under the Open Source Intelligence Lookups section.
The service provides insights into the reputation associated with the URL, showing which component of the file the verdict pertains to.
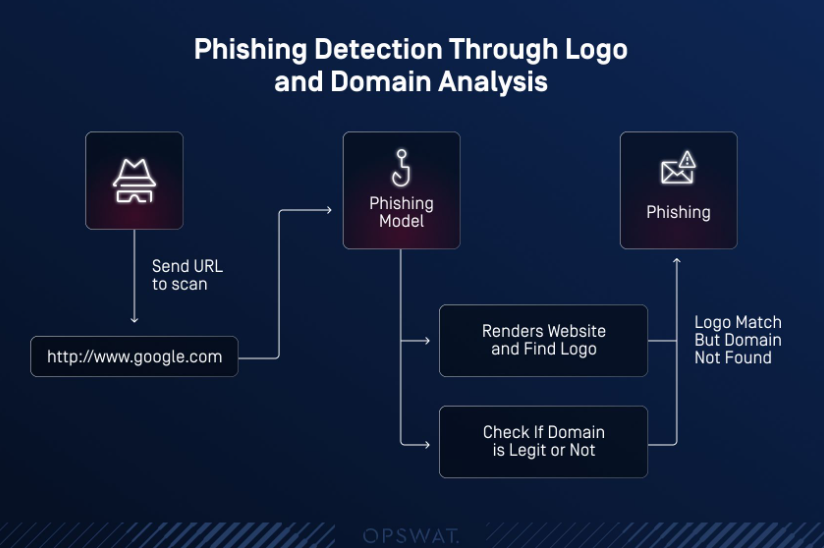
Phishing Detection Using Logos and Domain Analysis
Why does it matter?
The URL model is a great approach, but analyzing the URL alone is not enough to determine whether a website is phishing or malicious.
Since phishing remains one of the most prevalent forms of cyberattacks, our phishing detection model combines logo comparison with domain validation, creating a two-pronged defense system.
Logo Comparison
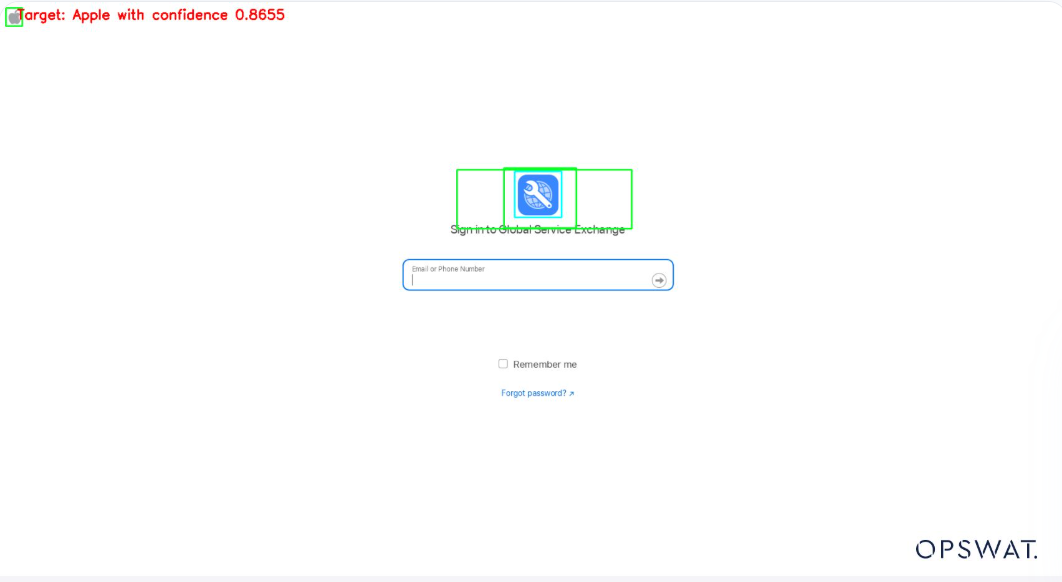
Using advanced computer vision algorithms, the model detects subtle differences between genuine and fraudulent logos.
For example, slight pixel distortions or changes in proportions that might escape human notice are flagged as suspicious.
Domain Validation
The model cross-references URLs with a database of known legitimate domains. If a mismatch or irregularity is detected, the system raises an alert.
Use Case
Imagine a phishing email claiming to come from a well-reputed bank, complete with a realistic logo.
The user might be fooled into clicking on it, believing the email is genuine.
Our model can instantly verify the logo’s authenticity while validating the email’s domain, stopping the attack in its tracks.
Outcome
Phishing is the most common type of cyber threat, often leading to data breaches, financial losses, and serious damage to a company’s reputation.
What’s worrying is that traditional URL-based phishing detection methods are often insufficient, with attackers frequently using legitimate-looking URLs and logos to deceive users.
To address this, we’ve incorporated logo comparison and domain validation to our URL model, improving its ability to catch phishing attempts that would normally bypass traditional defenses.
This improved URL model leads to a stronger, multi-layered defense against phishing, helping security teams respond faster and more accurately, and ultimately preventing attacks from causing any damage.
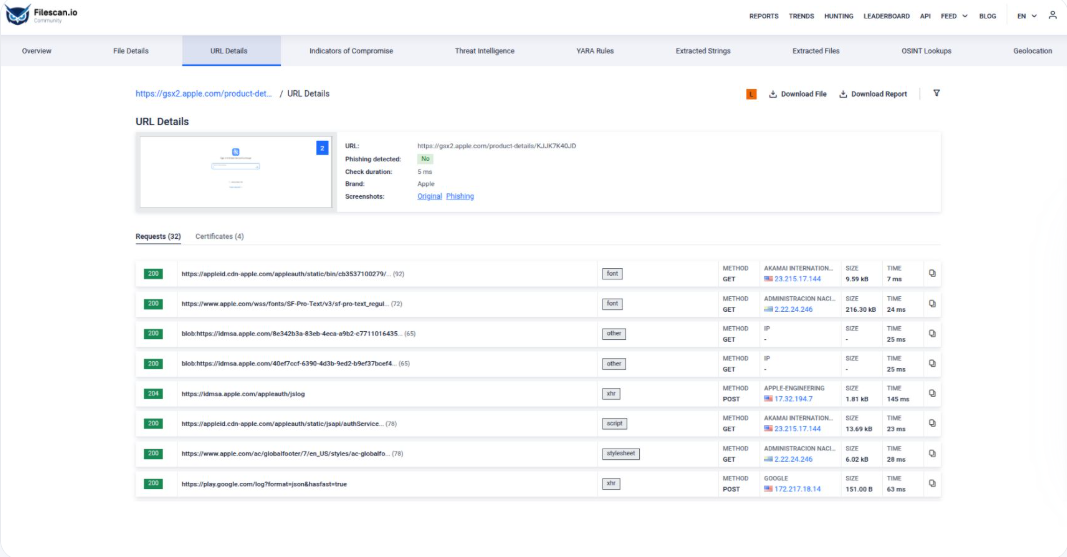
How to use Phishing Detection Using Logos and Domain Analysis in MetaDefender Sandbox™
- Scan a phishing website.
- Open the URL Details tab to view results.
- On the URL Detail tab, you’ll see the rendered page and the detected logo.
- You can find more detailed settings here.
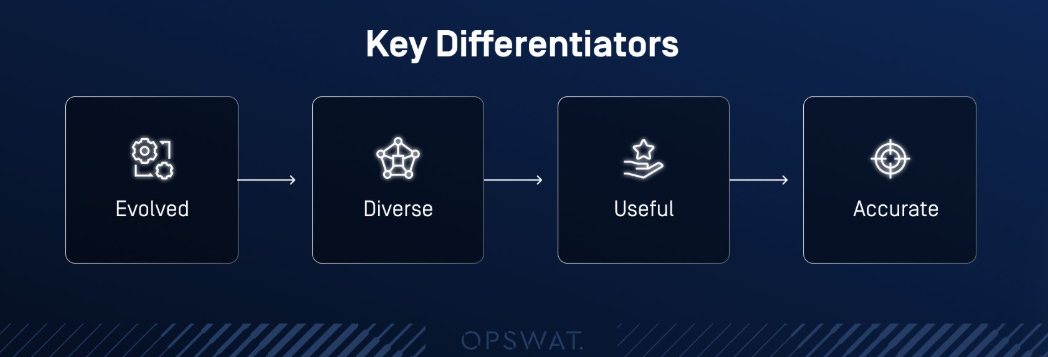
MetaDefender’s Unmatched Edge in the Data Science Landscape
- Evolved: Staying one step ahead of malicious trends, providing integrations that are as robust as they are reliable
- Diversed: to cover all the multiple facing problem we should provide a diverse AI toolset for different usecases
- Useful: Focus on what truly matters building tools that the market not only wants but genuinely needs
- Accurate: Ensure precision in integrations, as subpar tools undermine their value
AI-Driven Cybersecurity for the World’s Critical Infrastructure
The integration of AI into cybersecurity goes beyond performance improvement, completely redefining the cybersecurity landscape.
With solutions like MetaDefender Sandbox™, we’ve already begun transforming how organizations defend against the relentless cyberthreat landscape.
We didn’t just want to keep up with threats — we aimed to change the game entirely. By integrating next-generation technologies like AI-driven threat detection and predictive analysis, we’ve achieved that goal with MetaDefender Sandbox™.
The future is rich with possibilities and MetaDefender Sandbox™ is positioned at the forefront, offering tools like Similarity Search, ChatGPT-powered executive summaries, and advanced phishing detection models that are redefining digital security.
Our mission is simple: to empower security teams with the most advanced tools to protect their organizations from increasingly sophisticated attacks.
The journey is far from over, and we’re ready to lead the way toward a safer, more secure digital world.
Stay tuned — the future of cybersecurity is just beginning, and we’re driving it forward.